Analyze Database Audit Logs for Security and Compliance Using Amazon Redshift Spectrum | AWS Big Data Blog

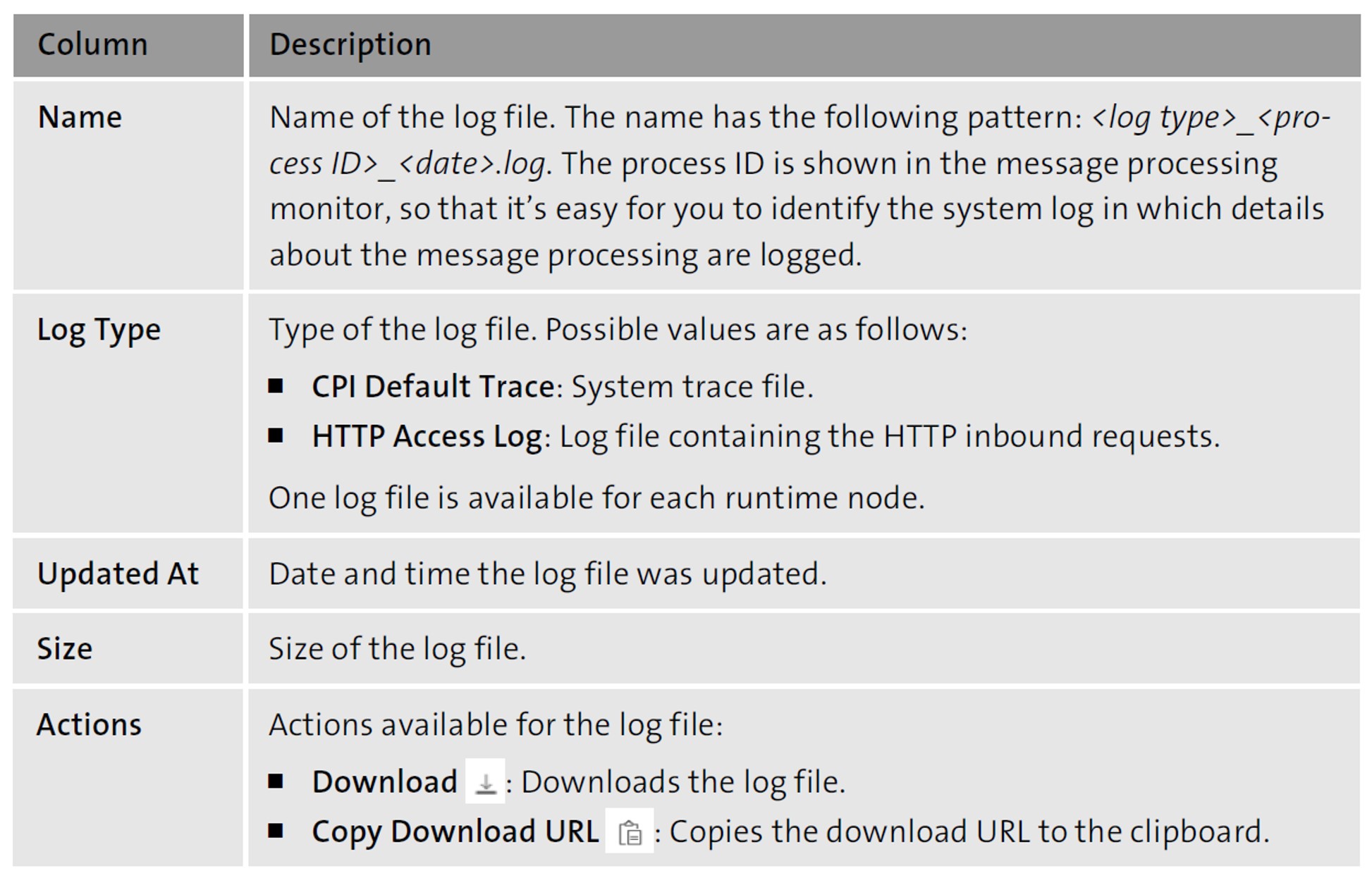
Configuring an audit log to capture database activities for Amazon RDS for MySQL and Amazon Aurora with MySQL compatibility | AWS Database Blog
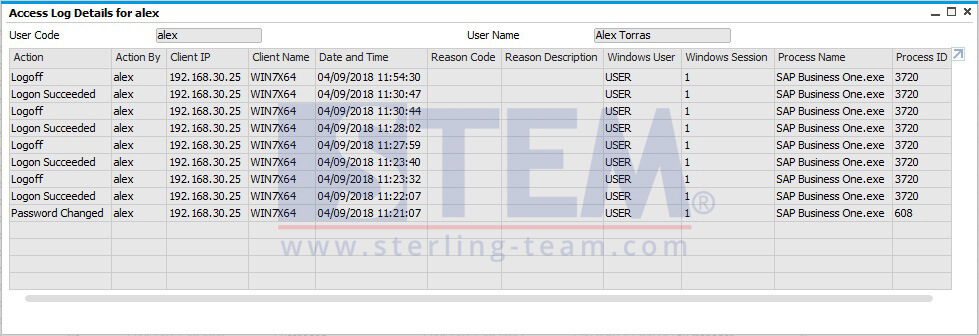
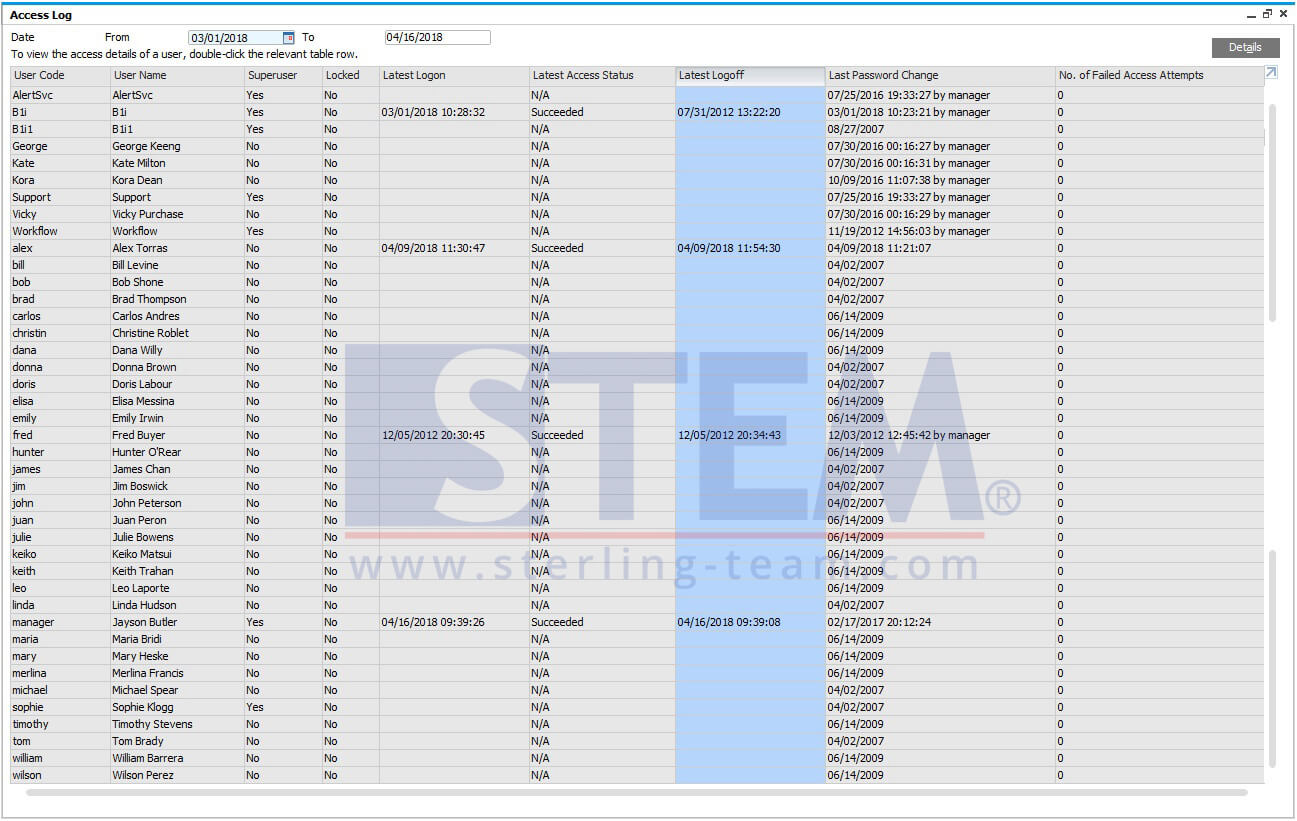
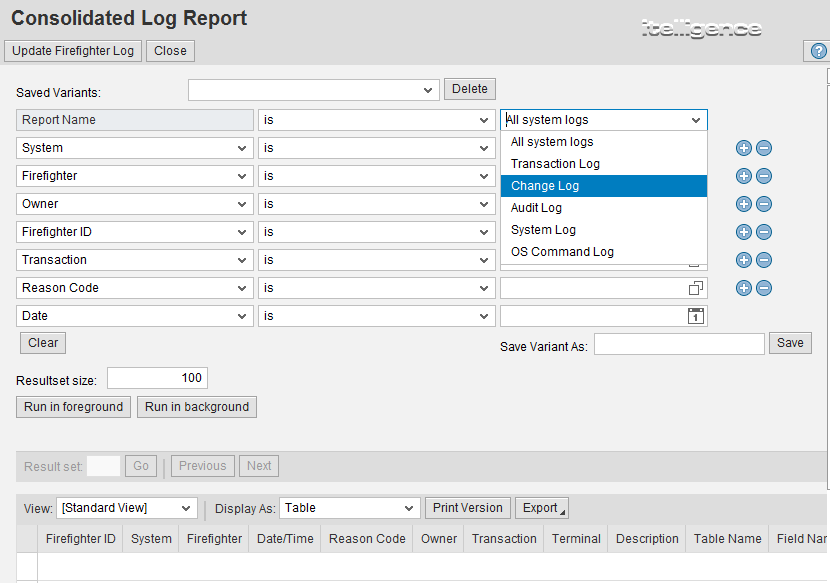
Monitoring Access Log & Change Log for Identify User Access | SAP Business One Indonesia Tips | STEM SAP Gold Partner

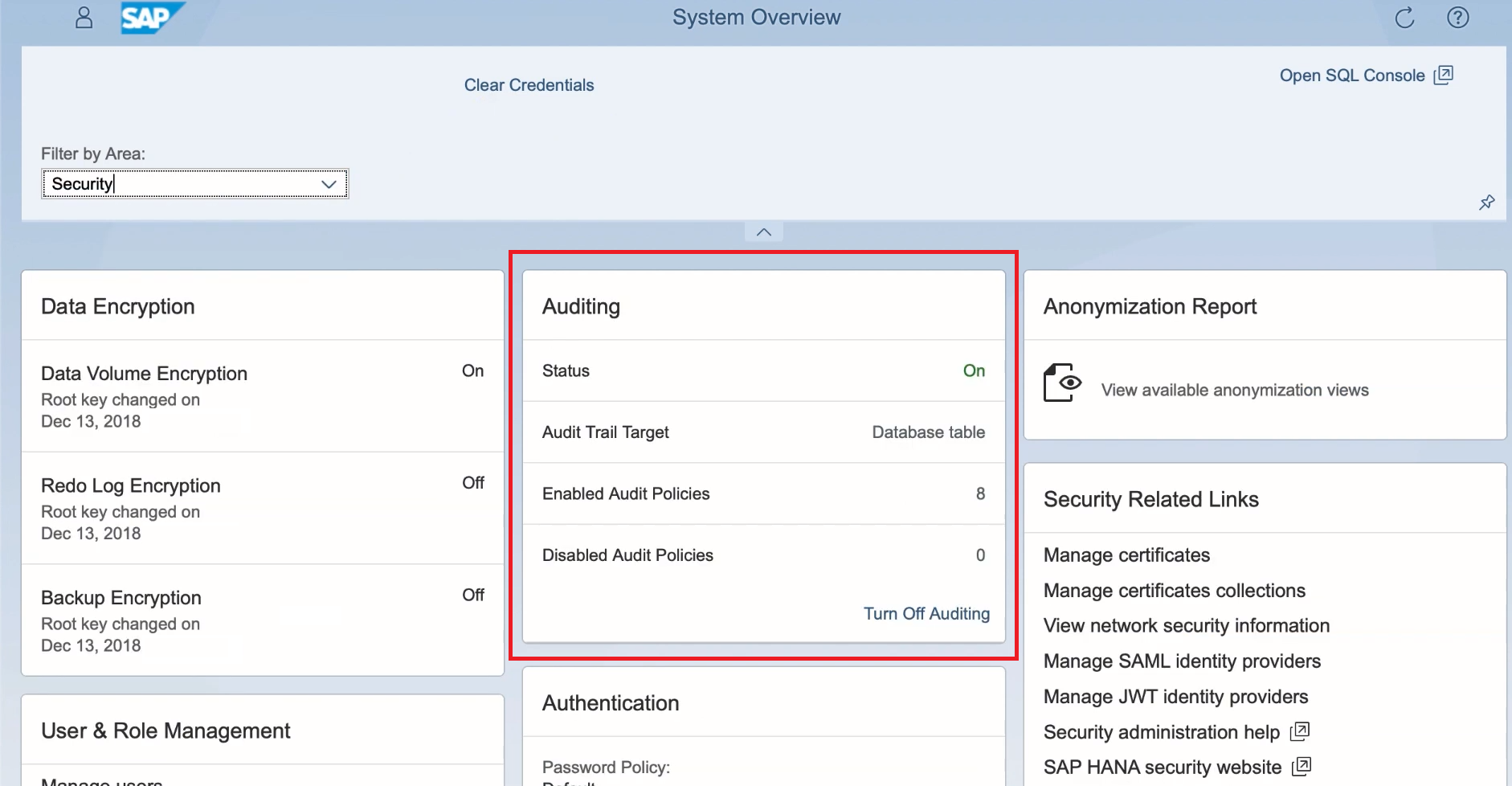
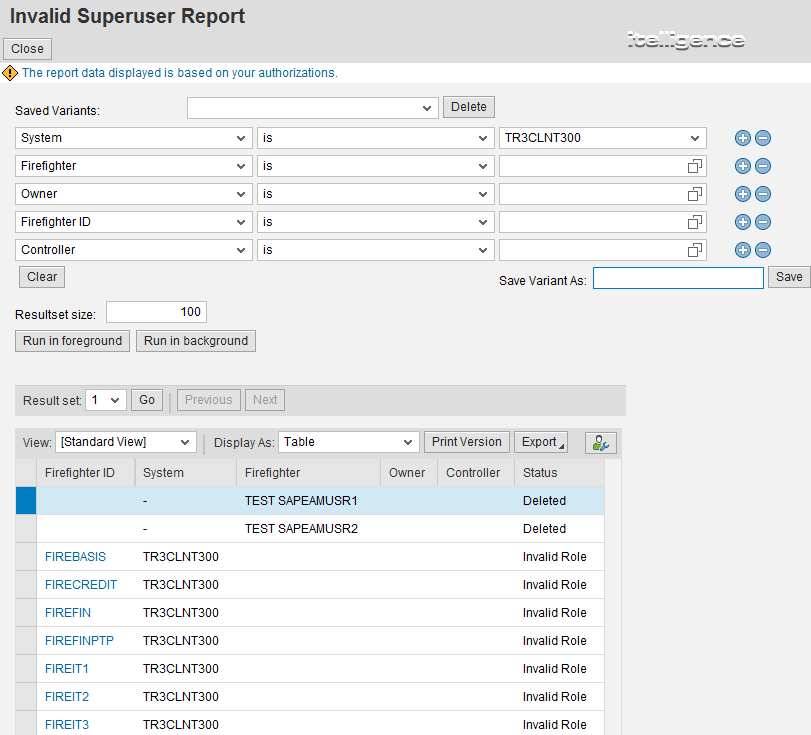
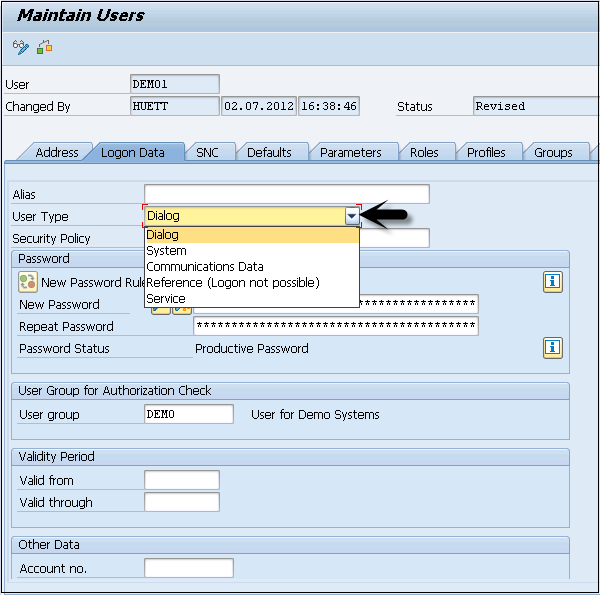
SAP Security Audit Logs: Which event types should I enable? There are 90 of them! And how much disk space do I need? | SAP Blogs
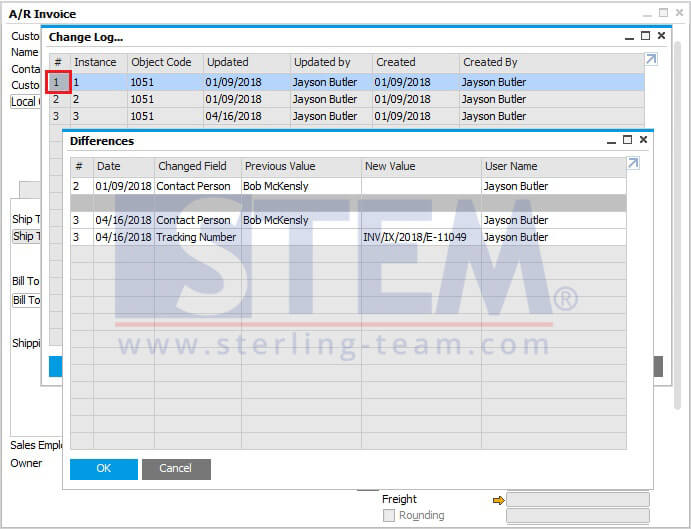
Monitoring Access Log & Change Log for Identify User Access | SAP Business One Indonesia Tips | STEM SAP Gold Partner