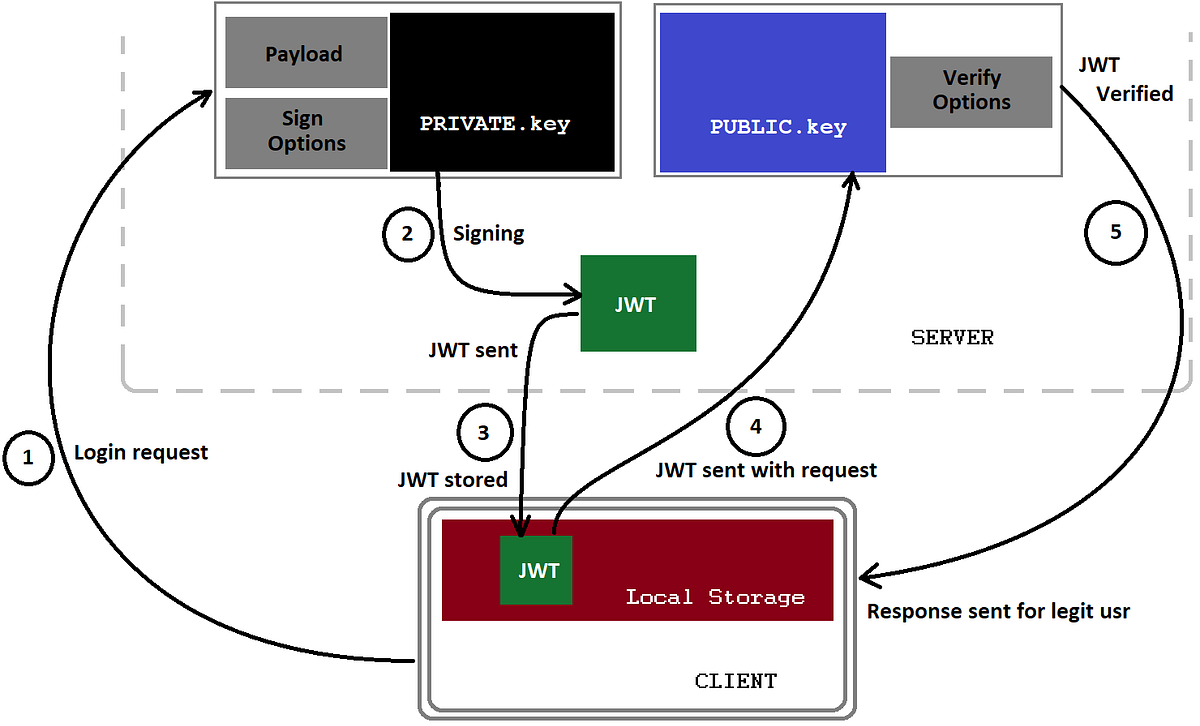
JSON Web Token (JWT) — The right way of implementing, with Node.js | by Siddhartha Chowdhury | Medium

How to Sign-In with Google in Angular and use JWT based .NET Core API Authentication (RSA) | by Christian Zink | Level Up Coding
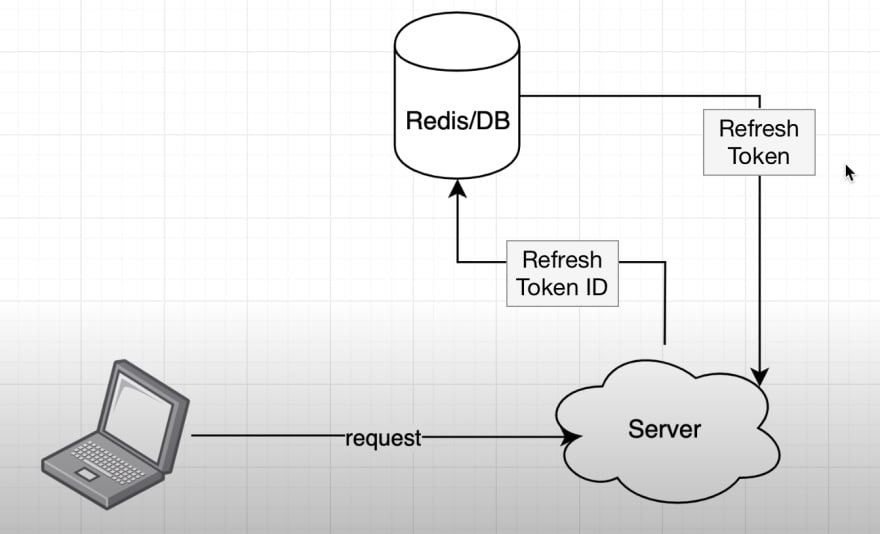
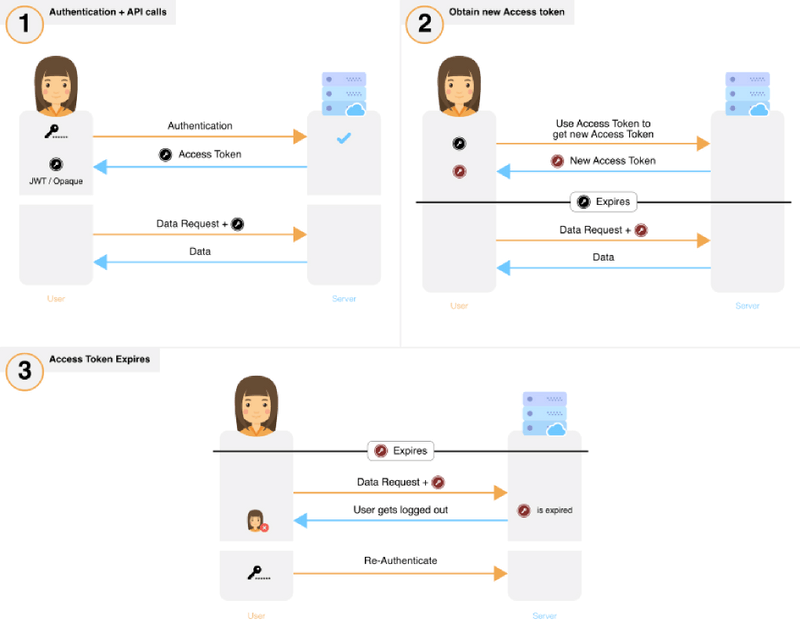
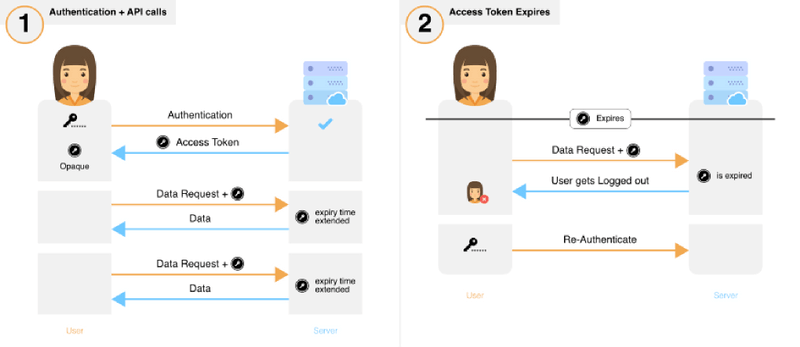
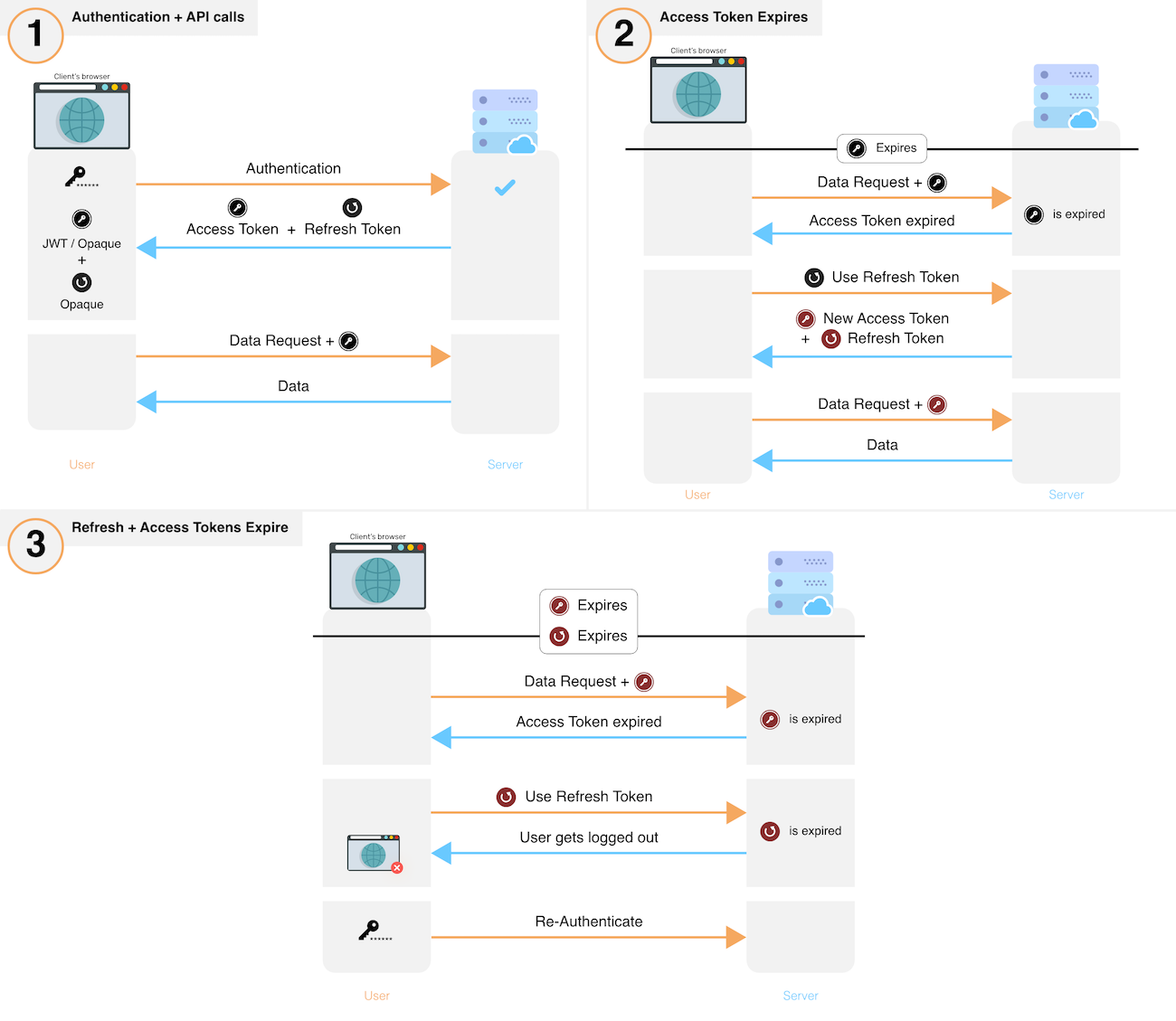
JSON web tokens are NOT meant for authenticating the same user repeatedly: Use session tokens instead - DEV Community 👩💻👨💻
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study | HTML