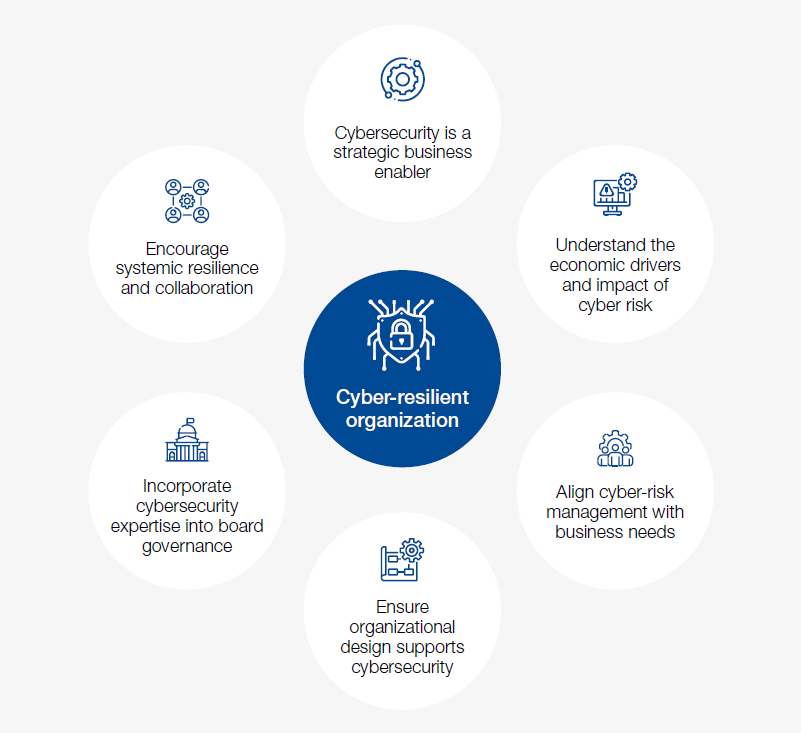
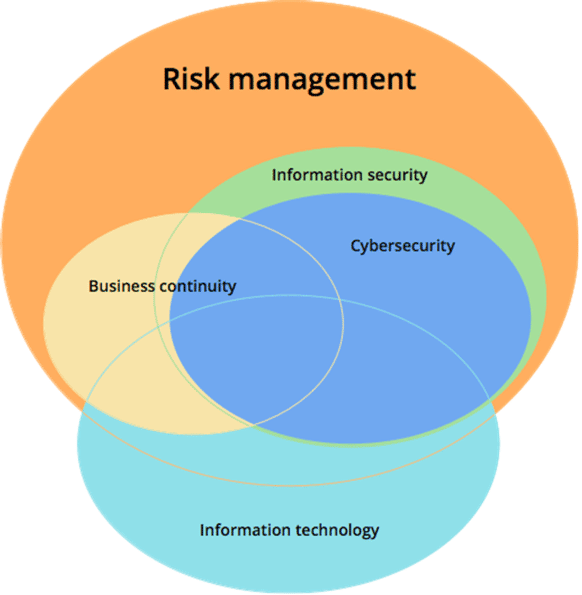
The Need for Information Security(1) Lecture 2. Slide 2 Business Needs First, Technology Needs Last Information security performs four important functions. - ppt download

How to organize your security team: The evolution of cybersecurity roles and responsibilities - Microsoft Security Blog
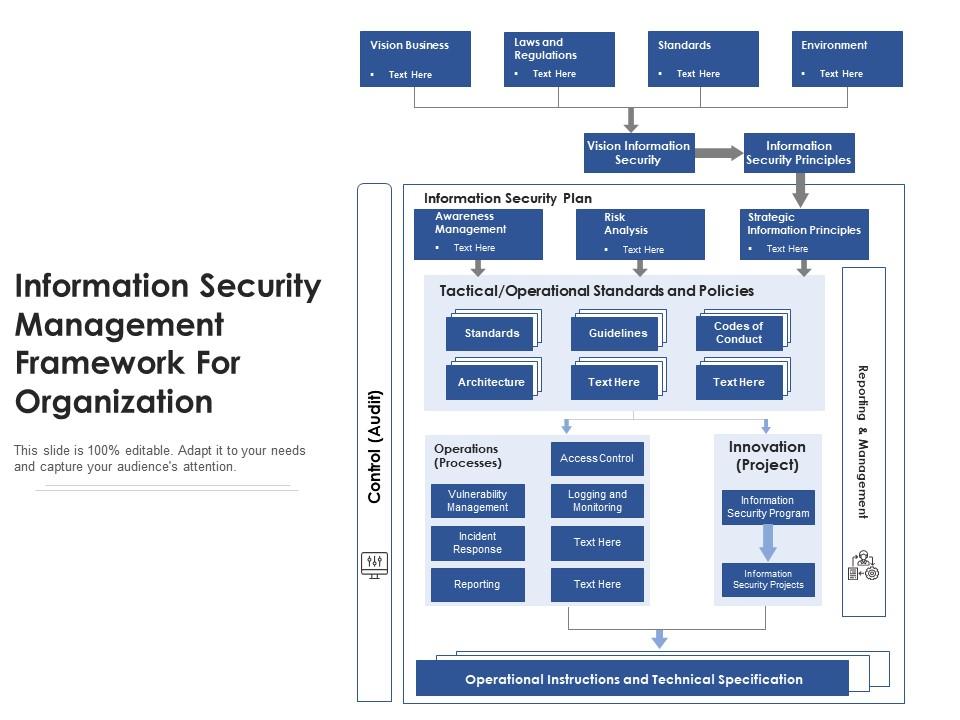
Information Security Management Framework For Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates