Implementation and Performance Analysis of True Random Number Generator on FPGA Environment by Using Non-periodic Chaotic Signals Obtained from Chaotic Maps | SpringerLink

Figure 3 from Implementation of the Binary Random Number Generator Using the Knight Tour Problem | Semantic Scholar
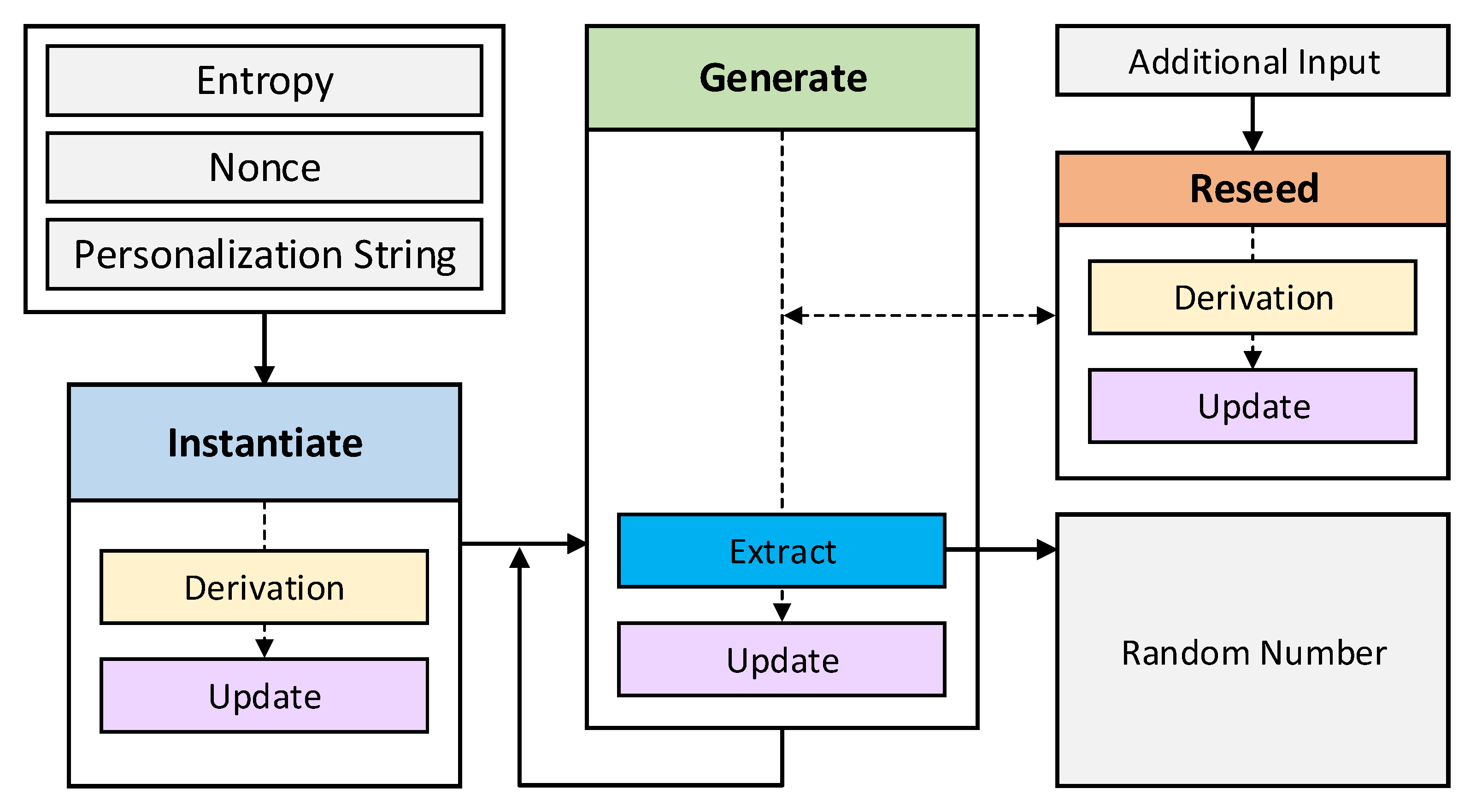
November 2014 version) - DRAFT Special Publication 800-90A Revision 1, Recommendation for Random Number Generation Using Determ

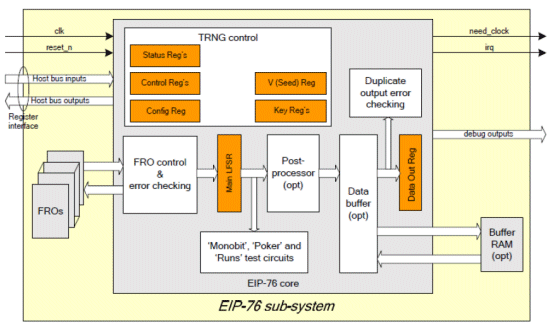
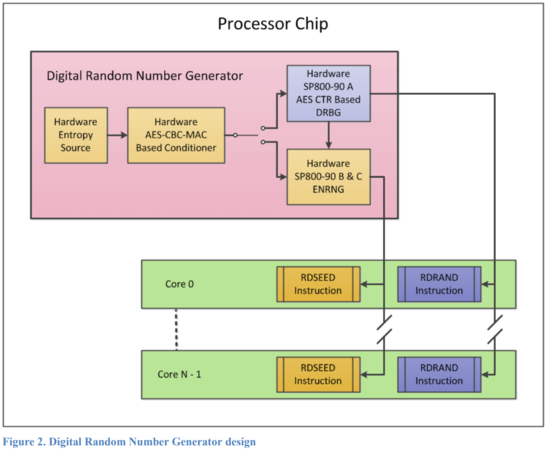
Building a Modern TRNG | Proceedings of the 4th ACM Workshop on Attacks and Solutions in Hardware Security
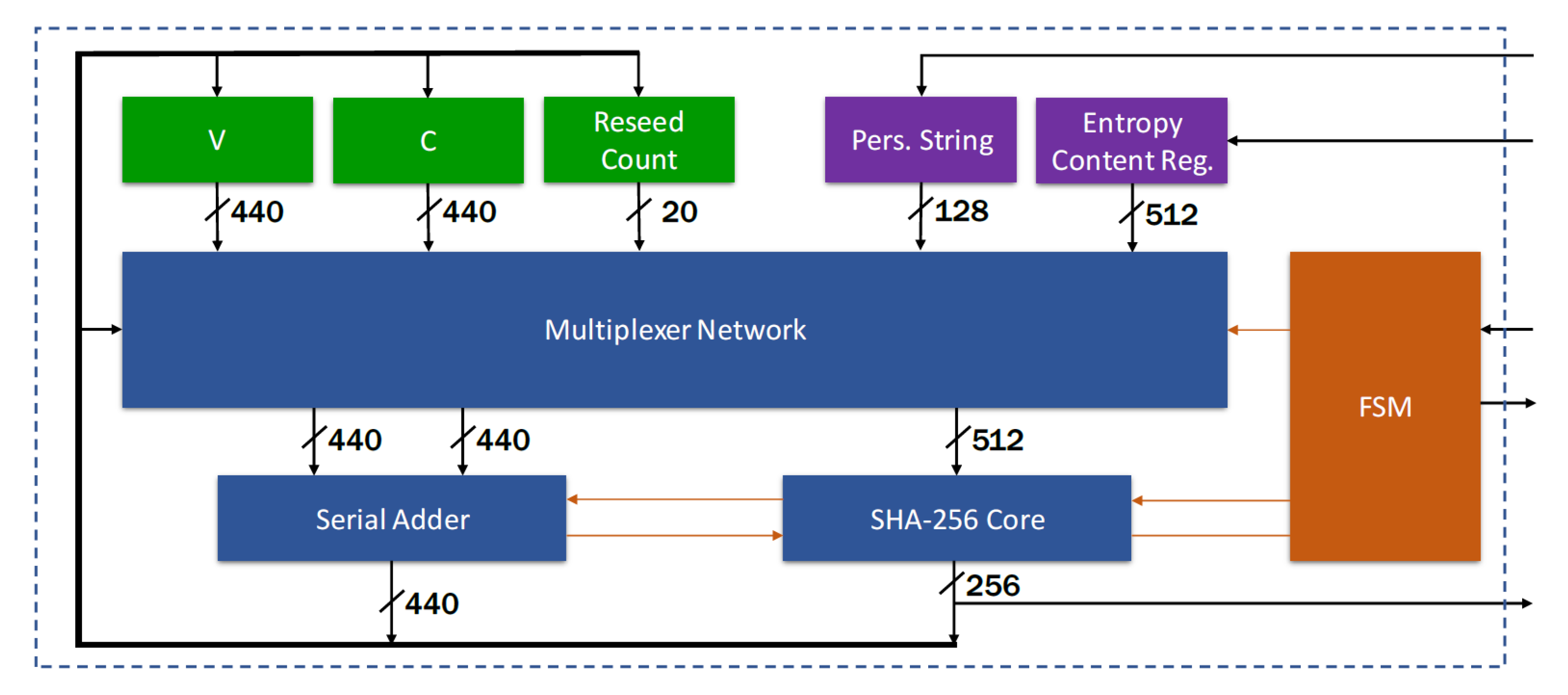
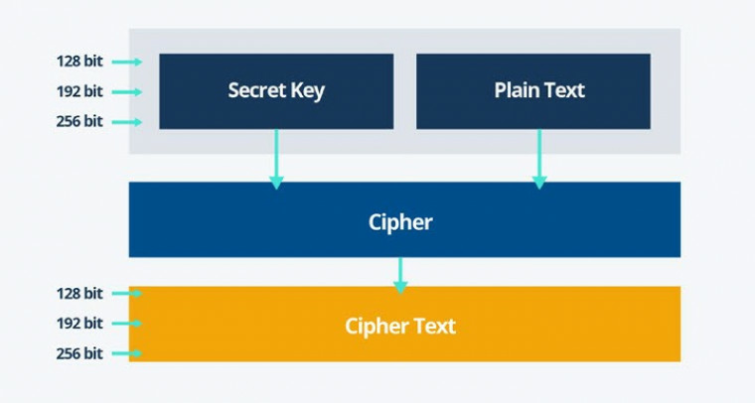
Sensors | Free Full-Text | Cryptographically Secure Pseudo-Random Number Generator IP-Core Based on SHA2 Algorithm | HTML