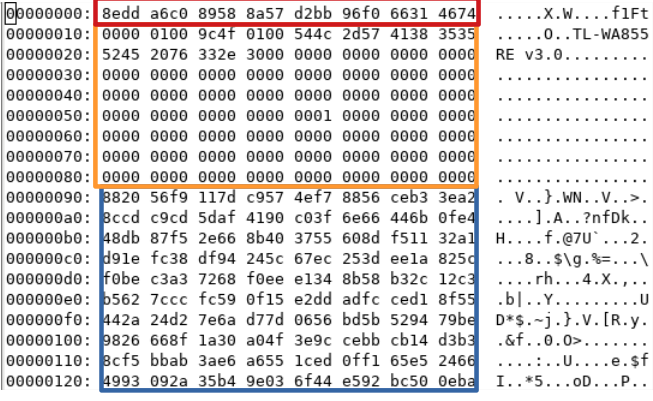
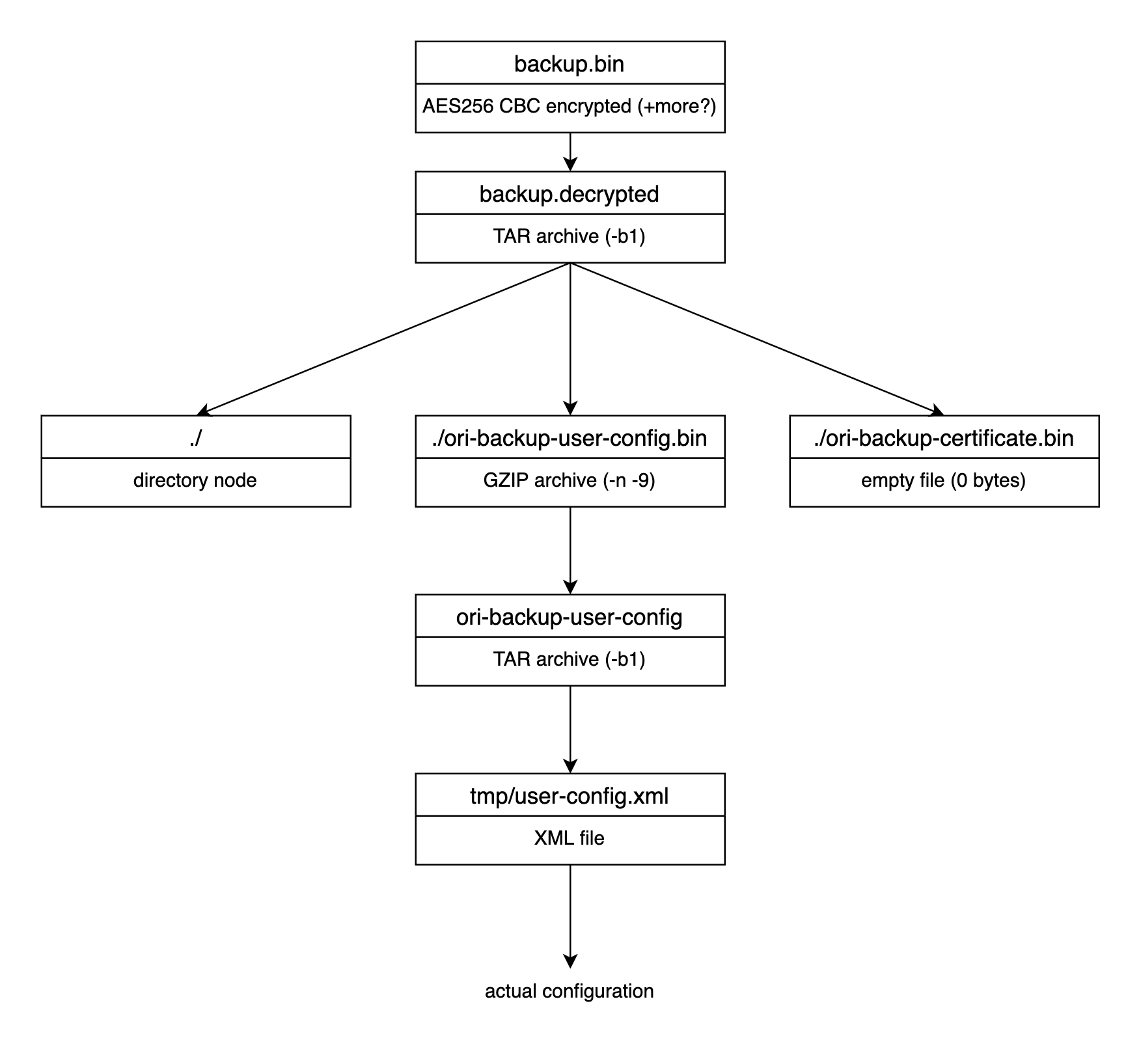
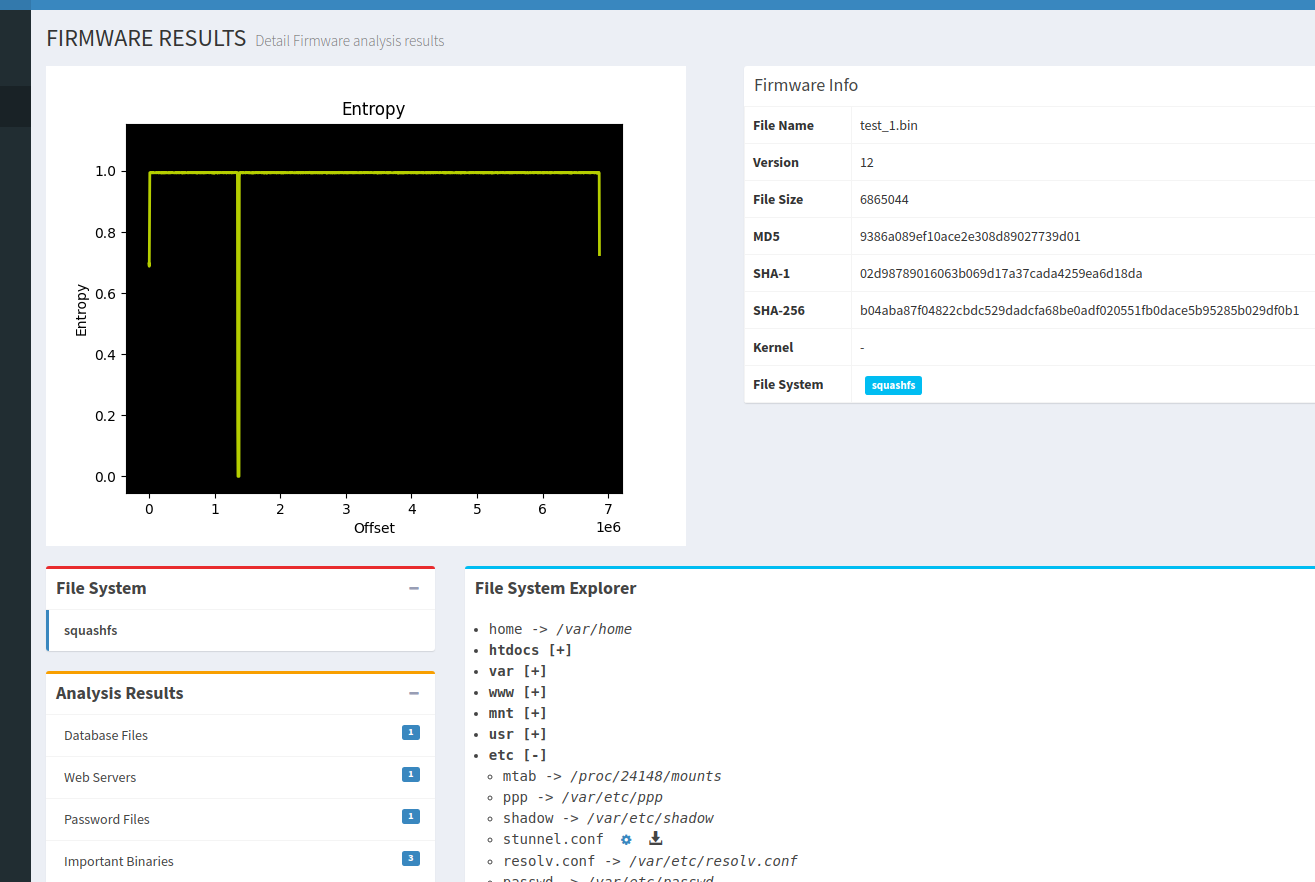
Tp-Link CPE-510/520 "new" Config.bin structure: Decryption, modify, re-encryption - Malware Analysis - Malware Analysis, News and Indicators
GitHub - sta-c0000/tpconf_bin_xml: Command line utility to convert TP-Link router backup config files
Breaking the D-Link DIR3060 Firmware Encryption - Static analysis of the decryption routine - Part 2.2